Wow! First place baby!
Here is a write up I did on a competition that took place at DEFCON this year. To be fair I should disclose that I work for Cybertap and work on the Recon product. The tasks where Recon was used could of course been solved using other tools, but when you have access to a network analysis tool designed for this sort of thing it really helps.
This year’s challenge had approximately 200 teams competing. The 2nd and 4th place teams from last year’s competition were also present. It took 4.5 hours to complete a total of eight rounds. The 2nd place team (the same team that came in 4th last year) took about 5 hours to complete the challenge.
Tools used
CYBERTAP RECON
Recon ingests real-time or archived (Pcap) network packets, decompiles all the flows and indexes every byte of information using a search engine. All network data is indexed including address and port meta-data, protocol meta-data, message contents, embedded file meta-data, and file content metadata.
WIRESHARK
Wireshark is a network protocol analyzer.
NETWORKMINER FREE
NetworkMiner is a Network Forensic Analysis Tool for Windows. NetworkMiner can parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
HXD
HxD is a fast free hex.
NOTEPAD++
Notepad++ is a free Windows based source code editor and Notepad replacement.
VLC
VLC is an open-source cross-platform multimedia player.
TRUECRYPT
Free open-source disk encryption software.
USEFUL WEBSITES
www.asciitohex.com – used to convert hex to ASCII text.
display-kml.appspot.com – used to map KML data to a Google map.
http://en.wikipedia.org/wiki/List_of_file_signatures – Website with list of file signatures.
Forensic Challenge
1. What day of the week is the meeting scheduled for?
Wednesday
Time to compete task: 15 mins
NetworkMinner was able to identify an IRC chat but some messages were hex encoded. We used Notepad++ to clean up the text in the hex encoded messages and then converted the hex to ASCII.
Original text:
How does Wednesday sound?
Cleaned up hex:
48 6F 77 20 64 6F 65 73 20 57 65 64 6E 65 73 64 61 79 20 73 6F 75 6E 64 3F
Converted to ASCII:
How does Wednesday sound?
Tools used:
NetworkMinner
Notepad++
2. What city are they meeting?
Las Vegas
Time to compete task: 46 mins
The solution for this one required multiple steps.
Using Recon we searched and found the word betty in an AOL email message that contain text about the meeting. Using the source IP address (172.29.1.50) and viewing the results in Recon’s surveyor we were able to step through all the documents pertaining to this address. One document that stood out was sent on port 1024 and appeared to contain binary data.
To extract the original file out of the pcap we used Wireshark. There’s probably an easier way to do this… Using this filter we were able to capture just the traffic from 172.29.1.50 on port 1024.
tcp.port == 1024 and ip.src == 172.29.1.50
The results were then saved to a new pcap using the File->Export Specified Packets option. Next we opened the new pcap in Wireshark, follow tcp stream (there is only one stream in this new pcap), and then saved as raw file.
We had a file that probably contained what we were looking for but no idea what the format was. The Linux file utility identified it as data (no help there) and stings did not produce anything useful. There was one of three possibilities… it’s compressed, encrypted, or junk data to throw us off. The hint that it was encrypted was this bit of text from the email:
Here is the password for where you should meet me: S3cr3tVV34p0n
We have a password and what we assume is an encrypted file so the next step is to just start trying various encryption formats to see if there was anything that could open it. After lots of wasted time trying different formats, TrueCrypt was tried with the S3cr3tVV34p0n password with success. The TrueCrypt archive contained a text document and a picture of Vegas.
Tools used:
Recon
Wireshark
TrueCrypt
3. What will Gregory die from, if he fails to meet with Betty?
Dysentery
Time to compete task: 16 mins
Looking at this pcap in Wireshark we found a session that contained both text and data. The text part contained “VID_20130705_145557.mp4” indicating the data was an MP4 file.
The session was saved in a raw format that included the extra text garbage at the start of the file. To figure out where the actual start of the MP4 file was we used a hex editor and searched for the magic number for MP4 files.
00 00 00 nn 66 74 79 70
Once we had the start of the file we just remove all the data. The file was then playable in VLC. The video shows a reference to the game Oregon Trail and zooms in on the word dysentery.
Tools used:
Wireshark
HxD
VLC
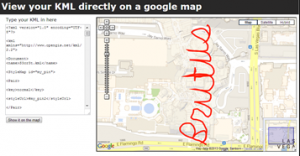
4. What is the password provided to Gregory?
Brutus
Time to compete task: 10 mins
Using Recon we found an XML file in the body of an email message. The file contents indicated it was a klm file.
KML is a file format used to display geographic data in an Earth browser such as Google Earth, Google Maps, and Google Maps for mobile.
To map the KML data to a Google map we used this site: http://display-kml.appspot.com/.
Tools used:
Recon
5. What happened to Gregory?
Unconscious behind recycle bin
Time to compete task: 60 mins
There was no pcap required to solve this round, just a dump of an Android smart phone. All the files from the dump were imported into Recon to make them searchable.
We were able to find text in a sent mms messages “I got the recipe for the toxic pumpkin pie”, but this was not the correct answer. Thinking maybe the message was hidden in an image we searched for just images and found one that provided the answer.
Tools used:
Recon
6. How many bytes of data is the malicious payload?
3113 B
Time to compete task: 4 mins
Processing the pcap in NetworkMiner the installed antivirus application flagged the 200912-paimia-&a.html file as malicious. Once we had the file name all that was required is to look at the size on disk.
Tools used:
Network Miner
7. What is the URL of the false(Malicious) web page Victoria is directed to?
bankofamerica.tt.omtrdc.net
Time to compete task: 67 mins
Lots of time was wasted examining javascript for a possible Black Hole redirection. The solution was found by searching for webhosts in Recon that contained bankofamerica but not part of the bankofamerica domain.
Tools used:
Recon
8. Who killed Gregory?
Victoria
Time to compete task: 5 mins
Recon extracted 4 voip files perfectly. Listing to the first file the caller (Victoria) admitted to the crime.
Tools used:
Recon