DEFCON 23 Network Forensics Competition
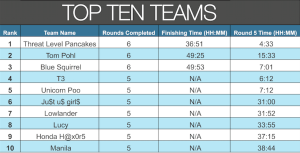
This year marked the fourth year participating in Network Forensics Competition and the fourth years of placing within the top three teams to finish. Similar to previous years, the competition consisted of six rounds plus one impossible to solve bonus round. Rounds five and six proved to be especially challenging this year due to the complexity of the rounds and two major mistakes that were made when round six was created. Only three teams completed all six rounds in the allotted time.
Our team (Blue Squirrel) consisted of four IBM employees and two from Sqrrl. This was the first year that we’ve partnered with another company.
IBM team members:
Darshan Gencarelle
Andrey Iesiev
Rory Bray
Yevgen Chernov
Sqrrl team members:
Adam Fuchs
Chris McCubbin
World’s most notorious hackers reveal their tricks at DEF CON hacking conference. @jeffrossen reports now pic.twitter.com/Y2QNMgtNaR
— NBC Nightly News (@NBCNightlyNews) August 10, 2015
DEFCON Files
I’ve created a zip file with the original DEFCON pcaps and all the extracted files for all the rounds. You can download the zip from here:
http://gencarelle.com/public_files/Defcon2015/defcon_2015.zip
Round 1
Truecrypt password: WhcFDjEQm9
Answer: Dimitri Bogomolovo
Tools used: Forensics, text editor, ROT13 decrypt (http://www.rot13.com/)
The attendees at this year’s DEFCON have noticed something strange. There is a man walking around screaming about how aliens have contacted him. If anyone actually stops and listens to him, he claims he can prove it because he captures his network traffic every night. Figure out who he is so we can look deeper into this.
What is the first and last name of the crazed patron?
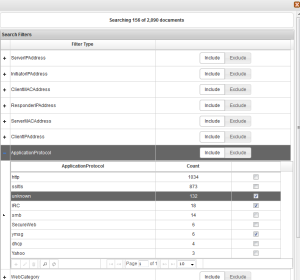
After importing the pcap into Forensics the first step is to eliminate non-relevant documents. Open the Filters window and expand ApplicationProtocol. Looking at the list of protocols in this pcap the most likely documents that will contain what we are looking for are IRC, ymsg, and unknown. Add these to the include filter.
Scanning down the Content field in the search results there is an “Unknown Session” document that looks interesting.
Click on the document to open. This appears to be some sort of chat. The only lines we are concerned with are the ones that begin with PRIVMSG.
Encrypted message:
PRIVMSG #meeh whfg urer jurer Nffhzvat svaq
PRIVMSG #meeh guvf zrff.
PRIVMSG #meeh obbgu cvpxvat pbagrfg whfg zrrg urer.
PRIVMSG #meeh gung gung pbaivaprq gung
PRIVMSG #meeh :nyvraf unir pbagnpgrq
PRIVMSG #meeh :Lrnu jvgu nyvra phgbhg fpernzvat. xvaq uneq zvff.
PRIVMSG #meeh zrna oryvrir nyvraf orpnhfr ernyyl yvxryl
PRIVMSG #meeh gung gurer ryfr gurer.
PRIVMSG #meeh nterr guvax gurl jnagrq pbagnpg gurl jbhyq pbagnpg fbzr penml
PRIVMSG #meeh xabj gung fubj nobhg nyvraf
PRIVMSG #meeh sbetrg jung punaary
PRIVMSG #meeh zrna Qvzvgev Obtbzbybib. Whfg orpnhfr qbra’g zrna yrff penml.
PRIVMSG #meeh argjbex npgvivgl pncgherq tvivat tenoorq orpnhfr yvggyr phevbhf. Rirelbar gnyxvat nobhg
PRIVMSG #meeh :Pbagrfg svefg ybbx yngre.
PRIVMSG #meeh :Njrfbzr fbba.
ROT13 decrypted message:
CEVIZFT #zrru just here where Assuming find
CEVIZFT #zrru this mess.
CEVIZFT #zrru booth picking contest just meet here.
CEVIZFT #zrru that that convinced that
CEVIZFT #zrru :aliens have contacted
CEVIZFT #zrru :Yeah with alien cutout screaming. kind hard miss.
CEVIZFT #zrru mean believe aliens because really likely
CEVIZFT #zrru that there else there.
CEVIZFT #zrru agree think they wanted contact they would contact some crazy
CEVIZFT #zrru know that show about aliens
CEVIZFT #zrru forget what channel
CEVIZFT #zrru mean Dimitri Bogomolovo. Just because doen’t mean less crazy.
CEVIZFT #zrru network activity captured giving grabbed because little curious. Everyone talking about
CEVIZFT #zrru :Contest first look later.
CEVIZFT #zrru :Awesome soon.
Round 2
Truecrypt password: 4TWSDjtAeb
Answer: 19bebeab4457def688c9520b28464157
Tools used: volatility, md5sum
During the investigation into the truth behind Dimitri’s statement, a image of his RAM was captured. We are trying to figure out if this is all in his head or not. Can you figure out what he has been up to lately?
1. What is the MD5 sum of Dimitri’s research file?
In this round we are investigating a memory dump. There’s lots of interesting and important stuff in the dump… always keep an eye out for solutions required in later rounds. Unfortunately there is also a lot of garbage that can lead you down the wrong path. I’ve listed the commands that proved to be useful.
volatility -f Round2.mem clipboard
– Extract the contents of the windows clipboard
Nothing all that interesting for this round but does include a hint for a later round.
volatility -f Round2.mem pslist
– Print all running processes by following the EPROCESS lists
Looking at the running processes we can see there are multiple notepads and one wordpad running. The text the user was typing is of interest.
volatility -f Round2.mem notepad
– List currently displayed notepad text
There are three files of interest. A file that seems to contain some sort of key and a gpg private key split into two files. The gpg key parts are for the same key so can be resembled back into a single file. Not what we are looking for this round but useful in a later rounds.
volatility -f Round2.mem cmdscan
– Extract command history by scanning for _COMMAND_HISTORY
The command history is a hint to put the two parts of the gpg key into a single file.
volatility -f Round2.mem iehistory
– Reconstruct Internet Explorer cache / history
Not much interesting here, with one exception. One file has a name that is an md5 hash.
volatility -f Round2.mem –dump-dir dumpdir memdump
– Dump the addressable memory for a process
This command will give us the text typed into the wordpad application. First thing to do is dump the running processes.
We know from the output from the pslist command that wordpad is process 1944 so we look for the 1944.dmp file. Dump all the strings from the binary file.
strings 1944.dmp > 1944.dmp.strings
Open the 1944.dmp.strings file and search down the file and you will find this text:
This is my research.
I believe that I have a newly implanted chip in my head.
The doctors scanned me and said there was nothing there.
I think they’re lying.
Save it to a text file named research and hash. Make sure you capture all the text, it has Linux EOL, and no trailing new line after the last line of text.
md5sum research.txt
19bebeab4457def688c9520b28464157 research.txt
This hash matches the one oddball filename in the IE cache file. This is the hash we are looking for.
I’ve included the output from the other commands bellow:
volatility -f Round2.mem pslist
Volatility Foundation Volatility Framework 2.4
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ———- ——————– —— —— —— ——– —— —— —————————— ——————————
…
0x861fb8d0 notepad.exe 2320 1840 1 37 0 0 2015-07-14 18:52:00 UTC+0000 0x85fa3020 notepad.exe 2376 1840 1 37 0 0 2015-07-14 18:52:02 UTC+0000 0x85ea4700 notepad.exe 2432 1840 1 37 0 0 2015-07-14 18:52:05 UTC+0000 0x86009a30 wordpad.exe 1944 1840 4 100 0 0 2015-07-14 18:53:31 UTC+0000
…
volatility -f Round2.mem cmdscan
Volatility Foundation Volatility Framework 2.4
**************************************************
CommandProcess: csrss.exe Pid: 616
CommandHistory: 0x12386f8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 5 LastAdded: 4 LastDisplayed: 4
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x758
Cmd #0 @ 0x12447f0: SUPER_DUPER_SECRET1.txt + SUPER_DUPER_SECRET2.txt > The_Key
Cmd #1 @ 0x12448f0: I have hidden my research
Cmd #2 @ 0x1244930: I hope the aliens don’t figure out I am on to them
Cmd #3 @ 0x12449a0: I am sure they implanted something in me to monitor me
Cmd #4 @ 0x1244a18: if you are human, good luck the world is counting on you
volatility -f Round2.mem iehistory
Volatility Foundation Volatility Framework 2.4
**************************************************
Process: 1840 explorer.exe
Cache type “URL ” at 0x18a6800
Record length: 0x100
Location: Visited:
…
Queen_Elizabeth@file:///C:/Documents%20and%20Settings/Queen_Elizabeth/Desktop/19bebeab4457def688c9520b28464157.txt
…
Last modified: 2015-07-08 16:24:46 UTC+0000
Last accessed: 2015-07-08 16:24:46 UTC+0000
File Offset: 0x100, Data Offset: 0x0, Data Length: 0xe4
volatility -f Round2.mem notepad
Volatility Foundation Volatility Framework 2.4
Process: 2320
Text:
Text:
Open: 3,9
Closed: 4
Open: 25,1,22
Closed: 9,12,19,21
Open: 11,18
Closed: 2
Open: 10,16
Closed: 13
Process: 2376
Text:
Text:
8dagr1+7EiLkJER4JmBEy6owEZdPEQBt90S2QJ0DvgRVeE81AQgAnuVdCSsKR0O1
0sdaF3lYLZeluBdvC9/VR6MJtO72HFyxDEJ3iD46GptJC8ePvK+fUD/lc+s3gQUP
flPQy7iv651KcdVNvUKBoNUQtU5b97me2Egj4R7YnWbBk024G8qFRk/4if0TUCiZ
aOZRUytTa0IOksya4WupFzRQMq61pKUGz4XTlilLrN+c88AG9fQ4/+jvS/RRMEIZ
lkJDDsNomuuZZFqdtSORvsDv4eeZ918NB/e7hizWBzlCA/Fl1uxlXt86/RVcdI0P
C4N2N3P3frRrjAQvxo6PIEw5gm6mQxjCXBDcVe74mzGQwFordcJ+rF9nV6O0ZOUl
yooPIucQcQARAQAB/gMDAhDdgA/GJMA+0B8Y4lOIBo3dlKMdQuNJCqUS5JjRKF+a
T/ij2aWKleX/7xeEe/28Oz7oYy/KyalRyP9NXRG8+YGHUVH/BMUKYbom3Mhis/Dr
aETbcaVYlyiko9eK1blBG3FOCO/aLFxQMrHT1gN9CF2JK2iUX86NwhU1Eq5OYptu
J9yw8190zP3qnKhvdwV0kkawK8a0wwofb6eAt9H3y9YM3YIsNRKRVRUeWzntp6dK
IHGnbVN0bU6olvUueTusGbrrBuATx6V2A6NJAR+wStQyapdFOBVGnu8Fxq3GwQW/
PXvXapjrFXvv1Rf+oSxboiOgoq4J3ErfD6GVda1ZjpVoaAPt+z+XHK8SJTa0VwWy
HZ0P5WlhM+oIix20uYEYnPOPsXqw5/laqoBDNF39RVt1bnHz9l13WpYa3IC7uJgT
o61v5+z3Edj0z/rmG69gAS0oEaCv++lIoDIFi5LyRvPrf89R2i6f51dmuyCAsHto
qrwKSkza+xbKJaGSwQHKBI2qHbAjDvLlRekRaLzBFYyZHD+rmrzfJnioloBVtGTx
HmfEY9HXAMNWDi9xypYArXS10oswe8nUmvMn+gqYnjSwOadaOsTAT6sJUnxLV2/U
in4/tb1JIG0Rn0LMKOpj2BCnMee9vA14FRHk3PJ5qNUObX7n3R5f11PYc4q2sQzQ
BD5p+h7gNNd9VPp3zcLJhToVWgA8FDMff6EUabHJMOkmdXI6I3hfp5XbJPeHyRZv
hGN4M7SuVMsmHaem86eVTp1V+mSYDemMxnNQ1uw36hQMPPwzbIoAbbUSNYhIb1Qm
mJ4fiMJSAMPmAiKu2dY+xZOlmWEnOYU2wHeN8cyHCElh+rVZmXYxdmlS5F5SRC7c
EOhwInqkJYDnn6Hpe8PL1+u/rB2GDyph1+Bnrj+JASUEGAECAA8FAlV4TzUCGwwF
CQeGH4AACgkQOUxGFasYh551yAf9EARlLhREdp/w7GjUroIZSMZ1lJIcU3AJ8Vb+
lge/ZU5/nSkD0rPSrSp/nnrBhhpNgcMmaTPxr+RHK0bbK0JXeuHvFgmJjtBo8xSY
jdet6IxV2eR0J32yA1msRSJhmzpsQvD+n60l5qTwbT/DgBMe+dXnHc+OcdDZgQdH
+or0d8lS1ZEGZj/NBPA+kr7vimanyybqIT/WHhvuS5KrCi4rKleKcHG/oelk8chT
+QfHMLFtL/aTLt9Tupb7vazZIdjF65RmW1dvLD8bg3yamb7Yblv36XMnvB5yy8Tq
BOPWRGIFr14P0/6RRVh5hAdtV4vHp/jvYQPOUF8Ciho1cgH6lg==
=l4pC
—–END PGP PRIVATE KEY BLOCK—–
Process: 2432
Text:
Text:
—–BEGIN PGP PRIVATE KEY BLOCK—–
Version: GnuPG/MacGPG2 v2
lQO+BFV4TzUBCAD4CAngutPnU0fcvIxVSdKM8l/tGHSWlOg9bltmH+CRh197t+0z
W4nu3nefyFjXKRWunH90mRSsm/71DeKCnQw9EuNRVAiwh1I1bigcZwkLZCKoX3xn
HbD6WLMQ2EAaCIyHyzWvbqo9lsQRCcsyyUMJnLttTFGaWjw3omV0CQ4ZHthcpsDd
ME+Bb+i0D9jJc+aTbflo7y/IPM4yXSwlyG4x1XBL4TmDdnLQxNQPEPGiy+/kgIpm
58EGsyuzB1UNb9UWFdLpHgemKVzrpGGVRUm7aawPzlnjRFKEjRa4Ap9j8L+874nU
jtkiSpwPZskNuSa+0Fwk9Gjmbey8sug23WPHABEBAAH+AwMCEN2AD8YkwD7QXn1E
TUAFbyJkNbidPYoZXXnqAwycQ3J0rC2hDgVrbzm0JGDlLtxSZ6ZUBjXRzWdwLONo
lhaKCaS6zp73Wm7E9a+J088WT+3vcZb0t8Hc//WPXE1mz0qEwkBTnfpmUOPsNVav
Uarf7Vjp9VRUz5X2PmQ67WhxnZnmTKOv6wGW97F2dAg+T5D35GPkkfLcguIeBlnV
vx+ZuGFOP4T/KZiDtaBrryyGX7DPI/oQzK8s2Kd+jcf4TTaLWnAHCi1mYIVTs+MD
Ea9eyaXFHUna1jPyzcDgnJEghAvLg/d/OaCBN2AuW8Lh8tVajdYfEd5qjlcpjvLV
JkMdiua6IFei5mSmufADfFJx5vaGZBNJ8/9j6OoOUp6Vf4BOoXvPw25oB7ROCgqP
w0xjYZ9gX7qZ0j/20qHAFYQ7pNBlC7/GBT3iIrGQ1litCIxM3AizcAThjPnkbaFy
dqCKXLWg6B6cg6ll7buqW3QUtBvrANa1igONjDOk/CvdN39yn+vVZtZPFjkJ252f
i1JLRmDSZG0yJ611dOpPfSmJBVFysulKKNT1nwTLZrMdY7plUoPo0rgK+BD9L6EJ
mlDmikQBS9Ncyk6mvu9I928tFCCOHd/+0eIzjNO8Rf0Utf7PIOTTUOdFQce95N7U
Sok50NbtEwzw92P2sIEwwRR9GQyM9wJIoZE2sqaN4gb7n2qplBqhUG+ZGBYQnobB
H2n+whibMc/QGuAon+6lc9Kv9WjyN3YUqceaj17ZzKQ+Su+TCGgL/bvE3stFJhIJ
maYoTJBdW+EJffAjvlZm3Ax4lkoIk7ZKBs2VUsp4cyNwswmcBwpDVZJjZI48hTZ3
AJdJLHm8VY0uAgUFj6vvGvOCvmvnwggjLBOinzoLJJwxjoa0nHaZefCNTRo7Cumz
gLQoQWN0dXJpYW5zIDxicnlhbnRoZXNjaWVuY2VndXlAZ21haWwuY29tPokBPgQT
AQIAKAUCVXhPNQIbAwUJB4YfgAYLCQgHAwIGFQgCCQoLBBYCAwECHgECF4AACgkQ
OUxGFasYh56PHAgAx1C5eRtpQVVfRR7nekjekXW8xQk5zavgarVgGmial8at3n9K
xPPMJclFNCIreA6rry3NUhR3in0U/TV0j0+5NQDhprI5OeUg74O/xSCe72pJBYRl
TIJZM7zYb9CxMGoD0E36FSD0YUQaCD+UvH98nGAK+dJ5E3WRGN4gdp84gwATJeVH
JN+jmL0tOXXTOPNEZQ/V3H4pYnwIG+CBfzruRNv3eSqRlauj5eheTBmkAXtDEaCY
XQBJdbA/mF+6RrZPemyBjxQ06fFaJb0XeTH4R5Rq30ghIRLCuBqbMPBQLVGxsEY7
volatility -f Round2.mem clipboard
Volatility Foundation Volatility Framework 2.4
Session WindowStation Format Handle Object Data
———- ————- —————— ———- ———- ————————————————–
0 WinSta0 CF_UNICODETEXT 0x2a003f 0xe294d738 acturians first contact with stegosauruses
0 WinSta0 CF_LOCALE 0x60105 0xe274b4e0
0 WinSta0 CF_TEXT 0x1 ———-
0 WinSta0 CF_OEMTEXT 0x1 ———-
Round 3
Truecrypt password: jHfk4ykZBC
Answer: precious
Tools used: Forensics, text editor, Wireshark, Foremost, Audacity
Dimitri claims that he captures his traffic every day just in case he is ever contacted. This time it may have finally paid off! He believes he has actually been contacted by an alien race. Can you confirm if this is true?
1. What word was used to describe the Earth?
After importing the pcap into Forensics eliminate non-relevant documents. Open the Filters window and expand ApplicationProtocol. Looking at the list of protocols in this pcap the most likely documents are the ones containing Yahoo, and unknown. Select to add them to the include filter.
Doing a quick scan of the content field you will see there is a chat message similar to the first round. After cleaning up the text this is the conversation:
PRIVMSG #messages will never believe what happened just received strangest message.
PRIVMSG #messages :Yeah what even talking about?
PRIVMSG #messages :Check
PRIVMSG #messages :Yeah what this just noise. Weird just noise.
PRIVMSG #messages message from someone something.
PRIVMSG #messages nuts
PRIVMSG #messages what
PRIVMSG #messages :Because aliens
Time to find the audio file mentioned in the chat. A search for Filename:*mp3 produces no hits. Maybe just searching for mp3 will find something? The two documents are Yahoo Chat and contain the text blank.mp3. From this we know there was probably an mp3 file transferred that Forensics was not able to extract. We will need to dig a bit deeper using Wireshark, but first let’s narrow down what we need to investigate to just the two client IP address of the chat session.
PRIVMSG AND IPAddress:*
Looking at the IPAddress column we can see the both the server and client IP addresses of the chat conversion. We want just the private client address, 192.168.1.106 and 192.168.1.112.
Load the pcap into Wireshark and filter on the first IP address:
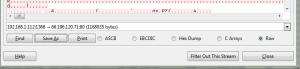
If you scroll down a bit there is an YMSG protocol packet that’s a “File Transfer Accept” which is very promising. Select the next packet (on port 80), right click and then select follow tcp stream.
We only want the data from the client to the server. Select the 192.168.1.112:1368 -> 66.196.120.71:80 traffic from the drop down, select Raw, and then Save As. Save the file as blank.mp3.
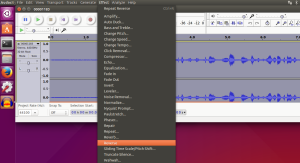
If you listen to the file in Audacity all you will hear is static. This is expected based on the chat message. The next step is to see if there is anything hidden in the audio file using foremost.
foremost blank.mp3
Foremost will find two mp4 files, 00000465.mp4 and 00001182.mp4. If you listen to then the audio it’s reversed. Audacity has an option under the effect menu option to reverse the audio. The 00001182.mp4 file has the answer.
Round 4
Truecrypt password: 86BNnSn7Jp
Answer: Arcturians
Tools used: Forensics
It turns out Dimitri isn’t as crazy as we thought! As we discovered, the aliens did in fact contact him. Time is of the essence, can you help figure out who is behind all of this?
1. What alien race contacted him?
After importing the pcap into Forensics the first step is to eliminate non-relevant documents. Open the Filters window and expand ApplicationProtocol. Looking at the list of protocols in this pcap http and unknown are where we will find the answer. Add them to the include filter.
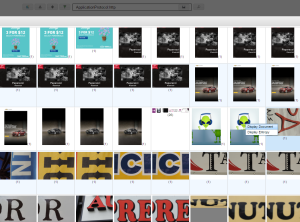
A few simple searches reveals there are no chats and nothing with alien, race, or Dimitri in it. Let’s take a look at the images. Search for ApplicationProtocol:http, change the grid size to 1000, select all documents, and then click the Image Analysis button.
The first thing to notice is there are a lot single letter images. Let’s see if we can filter out some of the non-letter images. Right click on one of the letter images and select Display Document.
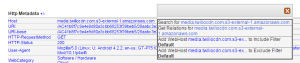
Under the Attributes tab right click on the host and select Search for. Close the document window and go back to the search grid.
Select all documents, and then click the Image Analysis button. We can see there are enough letters to spell a word but they appear to be all jumbled. Let’s see if they spell something if put in time order. This can be done in the surveyor. Close the Image Analysis popup.
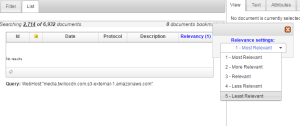
Select all document and then click on the surveyor button. Once in the surveyor change the Relevancy to 5 – Least Relevant.
Clicking documents in order and removing the doubles you will find the letters spell arcturians.
Round 5
Truecrypt password: djawp7Tw6W
Answer: Mega Death Ray 5102
Tools used: Aircrack, Wireshark, Forensics, Google
Word has spread about our confirmed alien contact and now everyone is trying to find them! A NASA scientist has even intercepted some traffic that looks rather suspicious. The only problem is we are unable to read it. Can you help us figure out what kind of traffic the scientist collected?
1. What technological instrument are they going to use to destroy the Earth?
Processing this pcap in Forensics produces 0 documents which is never a good sign. Opening in Wireshark you will see its all WPA encrypted 802.11 traffic. Wireshark can decrypt WPA traffic but we need the password.
In previous years it was made clear brute force cracking passwords should not be used as the passwords were very long and very random. Past rules apparently no longer apply as it’s the only way to find the WPA password for this round. The password is in the rockyou.txt password file. Here is the command to run the crack:
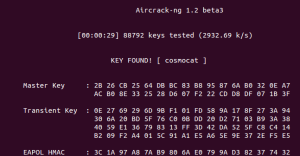
aircrack-ng -w rockyou.txt Round5.pcap
The password to decrypt the WPA traffic is “cosmocat”.
Using Wireshark you can now unencrypted the pcap with the password and save a new unencrypted pcap file. We can now use the unencrypted pcap in Forensics.
After importing the unencrypted pcap into Forensics we should again eliminate non-relevant documents. Open the Filters window and expand ApplicationProtocol. Similar to previous rounds we want only the IRC and unknown documents. Add them to the include filter. Scrolling over the results while looking at the Content column the first interesting document is an IRC chat with a PRIVMSG. Click on this document to open.
This chat has what we are looking for but it’s been encrypted in some way.
No Avatar Mon, 02:55 pm : PRIVMSG #Mothership :These humans are so dumb they will never figure out all the clues.
No Avatar Mon, 02:55 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :I know as time ticks down to the earth’s destruction I grow happier.
No Avatar Mon, 02:56 pm : PRIVMSG #Mothership :You seem particularly happy about it. Any reason why?
No Avatar Mon, 02:56 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :Of course we just finished a new weapon of massive planetary distruction.
No Avatar Mon, 02:56 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :Destruction*
No Avatar Mon, 02:56 pm : PRIVMSG #Mothership :I didn’t think that was finished. What’s it called again.
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :Oh yes it’s finished and we are going to try it out on earth first.
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :fde5020a5a97322bf5a7aee8174abbd8
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :d8c7d877ba6139c4872450e3847613a50c79f4e2
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :9406e3c325bfc9873426e5eda4ba6e18
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :0519a3b8d19f6d01501da1960c19385b5e938f86
No Avatar Mon, 02:57 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :I think it sounds powerful.
No Avatar Mon, 02:58 pm : PRIVMSG #Mothership :Yeah I would agree.
No Avatar Mon, 02:58 pm : PRIVMSG #Mothership :Have fun working on it. I wish I was assigned there.
No Avatar Mon, 02:59 pm vork: :vork!~bryan@162.219.72.250 PRIVMSG #Mothership :Well it is pretty awesome. But no rest for us. Talk to you later.
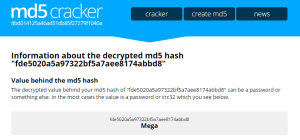
The encryption looks like an MD5 hash. Googling the first encrypted entry we find that it is.
To decipher the message Google each hash to find the corresponding word.
fde5020a5a97322bf5a7aee8174abbd8 = Mega
d8c7d877ba6139c4872450e3847613a50c79f4e2 = Death
9406e3c325bfc9873426e5eda4ba6e18 = Ray
0519a3b8d19f6d01501da1960c19385b5e938f86 = 5102
Round 6
Truecrypt password: hcdLwUKPTC
Answer: 08-21-51 13:37:54
Tools used: Wireshark, Forensics, TrueCrypt, quipqiup.com, gpg
It appears the aliens are preparing to destroy earth! This must be stopped! We have discovered some additional data that may be helpful in our efforts to protect earth. Unfortunately, the data is protected by a password that has yet to be cracked. Can you help us figure out how to read the secured information?
What time must the message be sent? Remember, time is running out! We need to know the exact time down to the very second!
Format of Answer: MM/DD/YR HR:MN:SC
The time is in military
Example Answer: 08/07/15 13:02:03
This round was very difficult and took the majority of time to complete. Additionally, there are two problems with this round that will make it virtually impossible to finish.
Any documents you can extract in Forensics are just a distraction. Using Wireshark you can see there is a large amount of network traffic between two IP addresses. Also, before and after this network traffic is series of SYN packets. The network traffic is a file transfer and the SYN packets is the key to unencrypt the file.
Use this filter in Wireshark to view the file transfer packets:
ip.src eq 192.168.1.5 && ip.dst eq 192.168.1.6
Ignoring the SYN and ssh packets we carved out the transfer and save to a file named mystery.pcap
Inspecting the contents of the mystery.pcap file we can tell it’s probably a Truecrypt volume based on the data seemed to be completely random, there is no file header, and the data is in multiples of 512 bytes. Now all we need is the password…
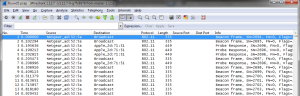
Remember the file from round two in the memory dump that had the Open and Close lines? Well, we need that now. Open is the Dest Port number of the series of SYN packets before the transfer. Close is the Dest Port number of the series of SYN packets after the transfer. The numbers in the file represent the SYN packet number starting at 1.
Open: 3, 9
Closed: 4
Open: 25,1,22
Closed: 9,12,19,21
Open: 11, 18
Closed: 2
Open: 10, 16
Closed: 13
Password for Truecrypt image:
94889488423292072372006423840394882920583871095838695030065838
Contained in the Truecrypt image file are two files:
- log – This is a bluetooth capture and can be opened in Wireshark.
- txt.gpg – This is a gpg encrypted file that we will need to decrypt.
A quick look at the bluetooth capture does not reveal anything obvious. Whatever is in the information.txt.gpg must hold the key. To decrypt the information.txt.gpg file we need the pgp private keys and the password. Both are in previous rounds.
If you remember back we found the private key in round two in the memory dump. It was split into two files. Here it is the complete key. Save the private key text into a file and then import into gpg.
—–BEGIN PGP PRIVATE KEY BLOCK—–
Version: GnuPG/MacGPG2 v2
lQO+BFV4TzUBCAD4CAngutPnU0fcvIxVSdKM8l/tGHSWlOg9bltmH+CRh197t+0z
W4nu3nefyFjXKRWunH90mRSsm/71DeKCnQw9EuNRVAiwh1I1bigcZwkLZCKoX3xn
HbD6WLMQ2EAaCIyHyzWvbqo9lsQRCcsyyUMJnLttTFGaWjw3omV0CQ4ZHthcpsDd
ME+Bb+i0D9jJc+aTbflo7y/IPM4yXSwlyG4x1XBL4TmDdnLQxNQPEPGiy+/kgIpm
58EGsyuzB1UNb9UWFdLpHgemKVzrpGGVRUm7aawPzlnjRFKEjRa4Ap9j8L+874nU
jtkiSpwPZskNuSa+0Fwk9Gjmbey8sug23WPHABEBAAH+AwMCEN2AD8YkwD7QXn1E
TUAFbyJkNbidPYoZXXnqAwycQ3J0rC2hDgVrbzm0JGDlLtxSZ6ZUBjXRzWdwLONo
lhaKCaS6zp73Wm7E9a+J088WT+3vcZb0t8Hc//WPXE1mz0qEwkBTnfpmUOPsNVav
Uarf7Vjp9VRUz5X2PmQ67WhxnZnmTKOv6wGW97F2dAg+T5D35GPkkfLcguIeBlnV
vx+ZuGFOP4T/KZiDtaBrryyGX7DPI/oQzK8s2Kd+jcf4TTaLWnAHCi1mYIVTs+MD
Ea9eyaXFHUna1jPyzcDgnJEghAvLg/d/OaCBN2AuW8Lh8tVajdYfEd5qjlcpjvLV
JkMdiua6IFei5mSmufADfFJx5vaGZBNJ8/9j6OoOUp6Vf4BOoXvPw25oB7ROCgqP
w0xjYZ9gX7qZ0j/20qHAFYQ7pNBlC7/GBT3iIrGQ1litCIxM3AizcAThjPnkbaFy
dqCKXLWg6B6cg6ll7buqW3QUtBvrANa1igONjDOk/CvdN39yn+vVZtZPFjkJ252f
i1JLRmDSZG0yJ611dOpPfSmJBVFysulKKNT1nwTLZrMdY7plUoPo0rgK+BD9L6EJ
mlDmikQBS9Ncyk6mvu9I928tFCCOHd/+0eIzjNO8Rf0Utf7PIOTTUOdFQce95N7U
Sok50NbtEwzw92P2sIEwwRR9GQyM9wJIoZE2sqaN4gb7n2qplBqhUG+ZGBYQnobB
H2n+whibMc/QGuAon+6lc9Kv9WjyN3YUqceaj17ZzKQ+Su+TCGgL/bvE3stFJhIJ
maYoTJBdW+EJffAjvlZm3Ax4lkoIk7ZKBs2VUsp4cyNwswmcBwpDVZJjZI48hTZ3
AJdJLHm8VY0uAgUFj6vvGvOCvmvnwggjLBOinzoLJJwxjoa0nHaZefCNTRo7Cumz
gLQoQWN0dXJpYW5zIDxicnlhbnRoZXNjaWVuY2VndXlAZ21haWwuY29tPokBPgQT
AQIAKAUCVXhPNQIbAwUJB4YfgAYLCQgHAwIGFQgCCQoLBBYCAwECHgECF4AACgkQ
OUxGFasYh56PHAgAx1C5eRtpQVVfRR7nekjekXW8xQk5zavgarVgGmial8at3n9K
xPPMJclFNCIreA6rry3NUhR3in0U/TV0j0+5NQDhprI5OeUg74O/xSCe72pJBYRl
TIJZM7zYb9CxMGoD0E36FSD0YUQaCD+UvH98nGAK+dJ5E3WRGN4gdp84gwATJeVH
JN+jmL0tOXXTOPNEZQ/V3H4pYnwIG+CBfzruRNv3eSqRlauj5eheTBmkAXtDEaCY
XQBJdbA/mF+6RrZPemyBjxQ06fFaJb0XeTH4R5Rq30ghIRLCuBqbMPBQLVGxsEY7
8dagr1+7EiLkJER4JmBEy6owEZdPEQBt90S2QJ0DvgRVeE81AQgAnuVdCSsKR0O1
0sdaF3lYLZeluBdvC9/VR6MJtO72HFyxDEJ3iD46GptJC8ePvK+fUD/lc+s3gQUP
flPQy7iv651KcdVNvUKBoNUQtU5b97me2Egj4R7YnWbBk024G8qFRk/4if0TUCiZ
aOZRUytTa0IOksya4WupFzRQMq61pKUGz4XTlilLrN+c88AG9fQ4/+jvS/RRMEIZ
lkJDDsNomuuZZFqdtSORvsDv4eeZ918NB/e7hizWBzlCA/Fl1uxlXt86/RVcdI0P
C4N2N3P3frRrjAQvxo6PIEw5gm6mQxjCXBDcVe74mzGQwFordcJ+rF9nV6O0ZOUl
yooPIucQcQARAQAB/gMDAhDdgA/GJMA+0B8Y4lOIBo3dlKMdQuNJCqUS5JjRKF+a
T/ij2aWKleX/7xeEe/28Oz7oYy/KyalRyP9NXRG8+YGHUVH/BMUKYbom3Mhis/Dr
aETbcaVYlyiko9eK1blBG3FOCO/aLFxQMrHT1gN9CF2JK2iUX86NwhU1Eq5OYptu
J9yw8190zP3qnKhvdwV0kkawK8a0wwofb6eAt9H3y9YM3YIsNRKRVRUeWzntp6dK
IHGnbVN0bU6olvUueTusGbrrBuATx6V2A6NJAR+wStQyapdFOBVGnu8Fxq3GwQW/
PXvXapjrFXvv1Rf+oSxboiOgoq4J3ErfD6GVda1ZjpVoaAPt+z+XHK8SJTa0VwWy
HZ0P5WlhM+oIix20uYEYnPOPsXqw5/laqoBDNF39RVt1bnHz9l13WpYa3IC7uJgT
o61v5+z3Edj0z/rmG69gAS0oEaCv++lIoDIFi5LyRvPrf89R2i6f51dmuyCAsHto
qrwKSkza+xbKJaGSwQHKBI2qHbAjDvLlRekRaLzBFYyZHD+rmrzfJnioloBVtGTx
HmfEY9HXAMNWDi9xypYArXS10oswe8nUmvMn+gqYnjSwOadaOsTAT6sJUnxLV2/U
in4/tb1JIG0Rn0LMKOpj2BCnMee9vA14FRHk3PJ5qNUObX7n3R5f11PYc4q2sQzQ
BD5p+h7gNNd9VPp3zcLJhToVWgA8FDMff6EUabHJMOkmdXI6I3hfp5XbJPeHyRZv
hGN4M7SuVMsmHaem86eVTp1V+mSYDemMxnNQ1uw36hQMPPwzbIoAbbUSNYhIb1Qm
mJ4fiMJSAMPmAiKu2dY+xZOlmWEnOYU2wHeN8cyHCElh+rVZmXYxdmlS5F5SRC7c
EOhwInqkJYDnn6Hpe8PL1+u/rB2GDyph1+Bnrj+JASUEGAECAA8FAlV4TzUCGwwF
CQeGH4AACgkQOUxGFasYh551yAf9EARlLhREdp/w7GjUroIZSMZ1lJIcU3AJ8Vb+
lge/ZU5/nSkD0rPSrSp/nnrBhhpNgcMmaTPxr+RHK0bbK0JXeuHvFgmJjtBo8xSY
jdet6IxV2eR0J32yA1msRSJhmzpsQvD+n60l5qTwbT/DgBMe+dXnHc+OcdDZgQdH
+or0d8lS1ZEGZj/NBPA+kr7vimanyybqIT/WHhvuS5KrCi4rKleKcHG/oelk8chT
+QfHMLFtL/aTLt9Tupb7vazZIdjF65RmW1dvLD8bg3yamb7Yblv36XMnvB5yy8Tq
BOPWRGIFr14P0/6RRVh5hAdtV4vHp/jvYQPOUF8Ciho1cgH6lg==
=l4pC
—–END PGP PRIVATE KEY BLOCK—–
gpg –allow-secret-key-import –import private_gpg.key
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
gpg: secret keys read: 1
gpg: secret keys imported: 1
Now to find the password. Going back to round one there was a second ymsg chat. Enter the following search in Forensics and select the second document.
ApplicationProtocol:ymsg
This is the raw chat with everything but the message removed:
Wrw blf ivnvnyvi gl hsldvi zmw kfg lm xovzm fmwvidvzi
uli WvuXlm?
Nln sld wrw blf tvg lm Ofpv’h xlnkfgvi?…zmw bvh.
Nln’h szev vbvh rm gsv yzxp lu gsvri svzwh…zmw z
gdvoev bvzi lowh kzhhdliw rh vzhb gl tfvhh.
Bvzs R tfvhh hrmxw rg’h qfhg rorpvzorvmh.
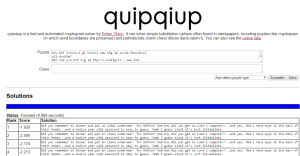
Unfortunately it’s not a simple ROT13 encrypted message. Let’s try http://quipqiup.com/index.php and see if we have any luck there…
Did you remember to shower and put on clean underwear for DEFCON? Mom how did you get on Luke’s computer?…and yes. Mom’s have eyes in the back of their heads…and a twelve year olds password is easy to guess. Yeah I guess sincd it’s just ilikealiens.
This is the first error in this round and probably show stopper without a bit of luck. The answer was supposed to be ilikealiens but it’s not, its ilovealiens.
Let’s decrypt the information.txt.gpg now. When prompted enter “ilovealiens” without the quotes.
gpg –output information.txt –decrypt information.txt.gpg
File contents:
Cyper
08/21/15 16:37:54
DATE: 2015-07-01
Weight:3
Minutes Awake:2
Gives Month
DATE: 2015-05-21
Calories Burned:1
Steps:2
Gives Day
DATE: 2015-05-17
Floors:2
Minutes Sedentary:4
Gives Year
DATE: 2015-06-03
Steps:2
Minutes Lightly Active:3
Gives Hour
DATE: 2015-06-09
Steps:1
Calories:2
Gives Minutes
DATE: 2015-06-27
Activity Calories:1
Distnace:3
Gives Seconds
This file this is key and the btsnoop_hci.log Bluetooth capture contains Fitbit log data that we can use with the key to find the answer. Open btsnoop_hci.log in a text editor and search for “text/comma-separated-values”. Save each CSV section to a text file. To make things easier open the CSV file in Excel. To find the date you need to search for the column on the given date and then use the number as the offset.
DATE: 2015-07-01
Weight:3
Minutes Awake:2
Gives Month
This is the second error with this round. This date does not exists! Let’s just assume we can make a few guesses and get lucky…. (We got it on the second try):
= 08
DATE: 2015-05-21
Calories Burned:1
Steps:2
Gives Day
2,030 ← Position 1
6,109 ← Position 2
= 21
DATE: 2015-05-17
Floors:2
Minutes Sedentary:4
Gives Year
15 ← Position 2
1,091 ← Position 4
= 51
DATE: 2015-06-03
Steps:2
Minutes Lightly Active:3
Gives Hour
6,144 ← Position 2
233 ← Position 3
= 13
DATE: 2015-06-09
Steps:1
Calories:2
Gives Minutes
3,885 ← Position 1
1,793 ← Position 2
= 37
DATE: 2015-06-27
Activity Calories:1
Distnace:3
Gives Seconds
577 ← Position 1
1.74 ← Position 3
= 54
Barring the issues with this year’s competition it was a lot of fun. Third place was Amazon Fire TV that no one on the team seemed to want. Maybe next year we can reclaim our first place position and have a prize worth fighting over. Thanks to everyone who not only helped during the competition but also worked to make Forensics a better product. If you are at DEFCON next year stop by the competition area and say hi.